A FULLY
Keyless Authentication
system
To enable physical and digital access.
Bringing Privacy, Security and Convenience.
THE PROBLEM
Shared Secrets
Passwords, keys, SSH keys. Weak and bad authentication is responsible for almost 80% of data breaches.
We’re solving the problem from its root by eliminating shared secrets from people-to-machine and machine-to-machine authentication.
PIN NUMBERS
PASSWORDS
KEYS
Solution
DYNAMIC AUTHENTICATION
Biometrics
Authentication Device
Embedded with biometrics: Smartphone, watch or chip
Authentication Cloud
Access everywhere
1 dashboard for all access management - 1 authentication device for all applications.


Technology
Shared Intelligence
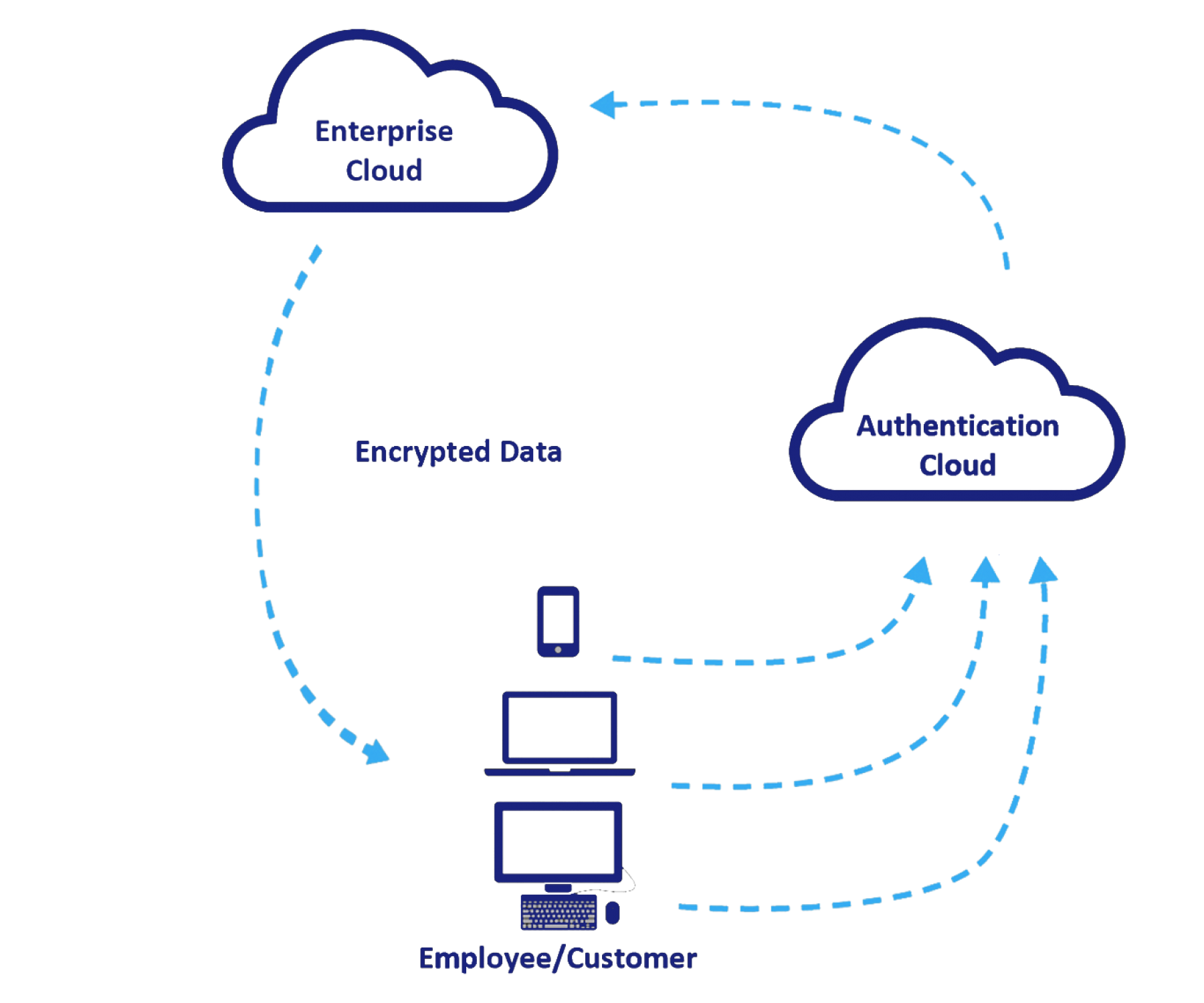
Technology
Authentication Layer

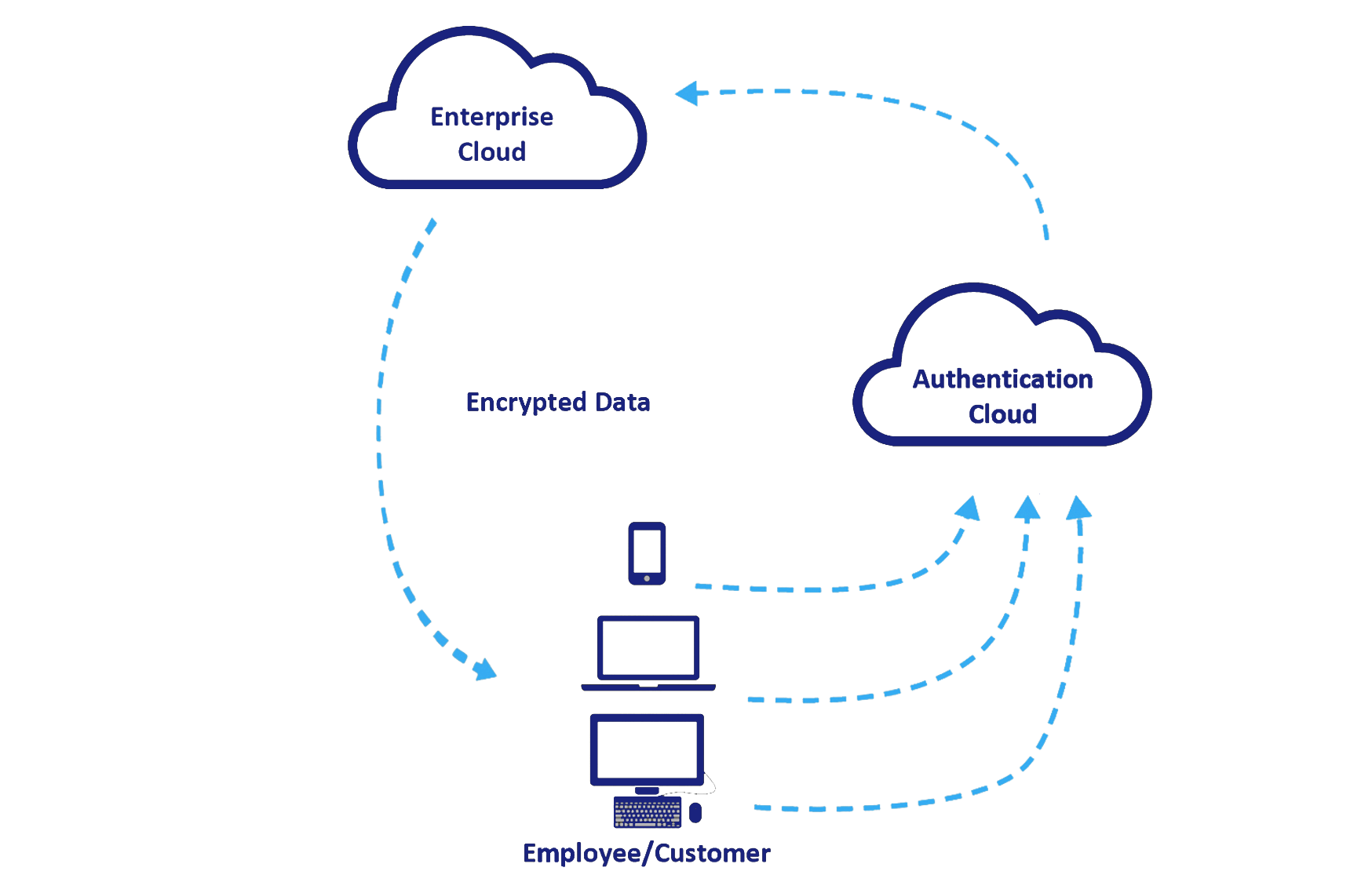
SERVICES
Authentication-as-a-service
Our authentication-as-a-service is easy to implement. An authentication layer is custom-built and deployed inside the perimeter to enable all authentications. One “plug-and-play” solution for all authentication needs.
One simple solution
One Authentication App
For users and enterprises, one simple app to manage authentication through a biometric smartphone
Available
For iris, face and fingerprint sensors
Integrated
4-way process that results in a dynamic encryption that changes in every attempt
Seamless
A hash of the pattern is stored locally in the device.
Propietary
An advanced deep learning algorithm analyzes them in the verification and recovery process.